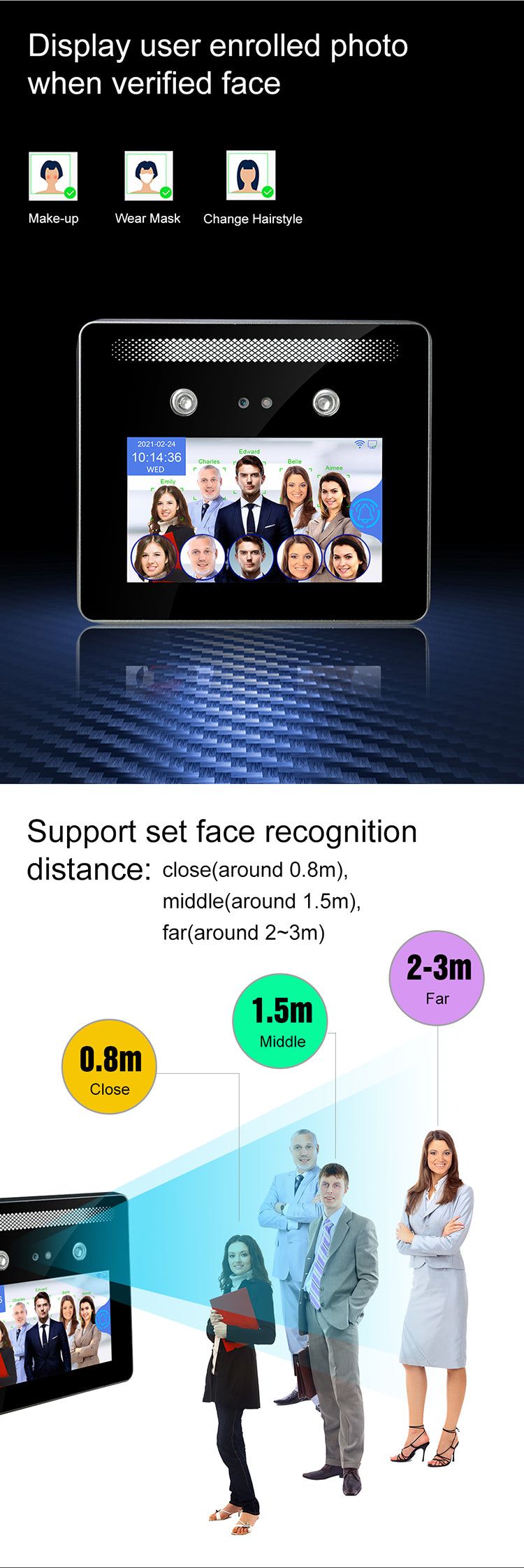
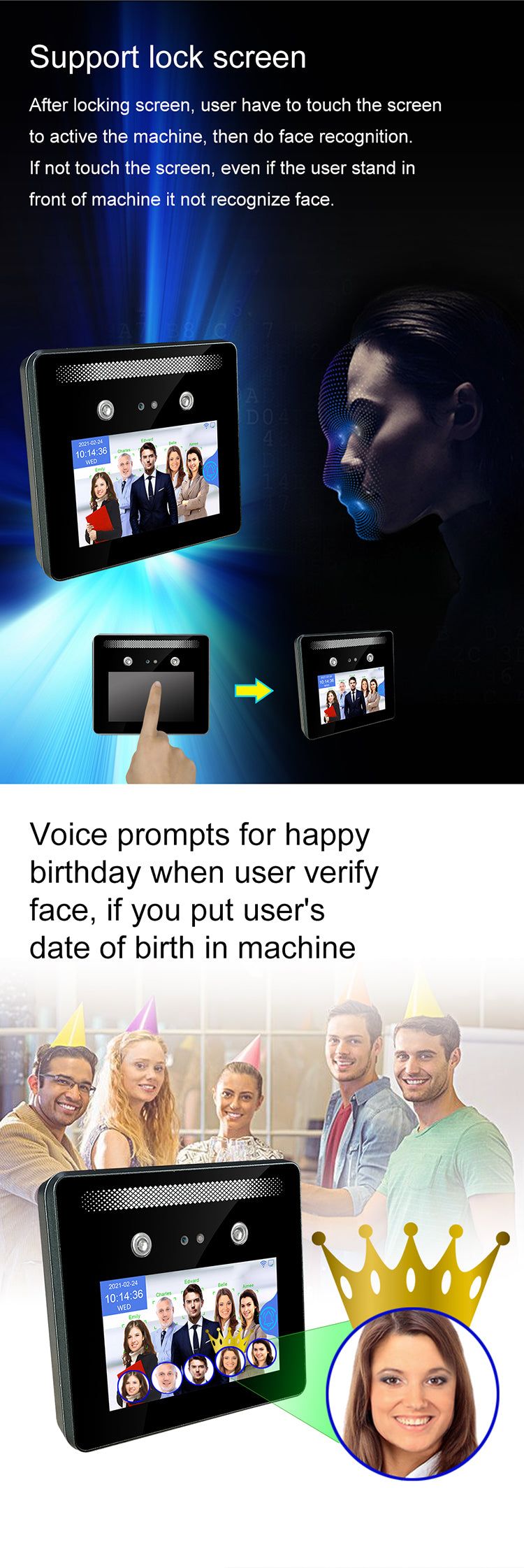
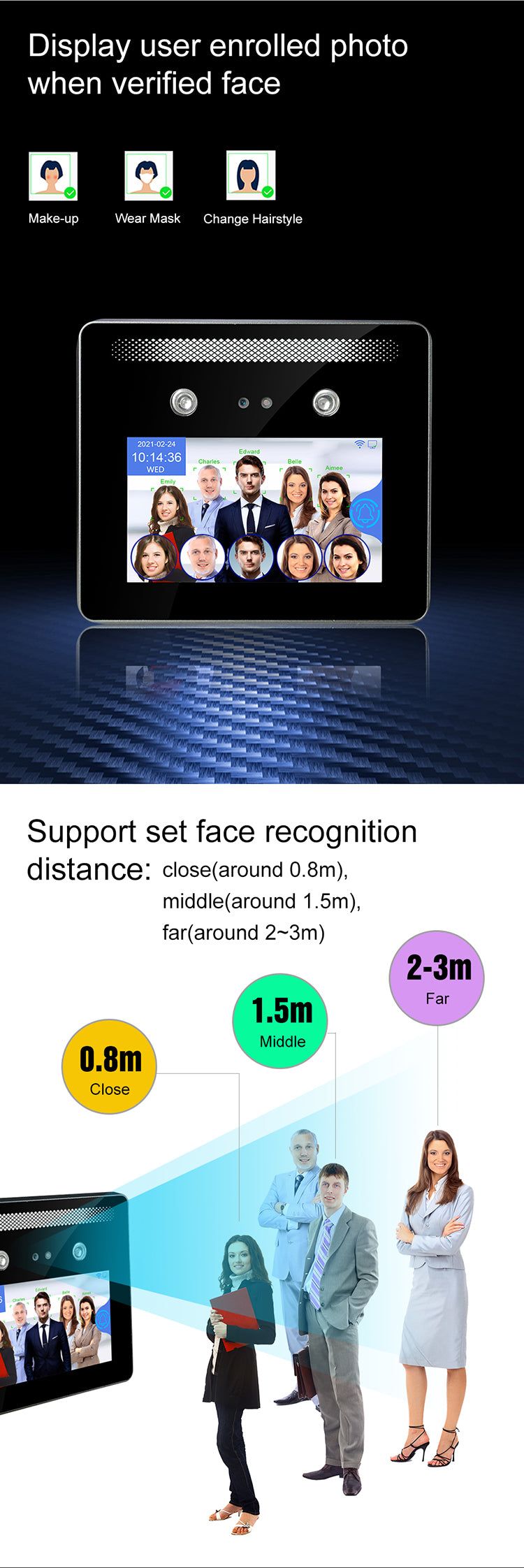
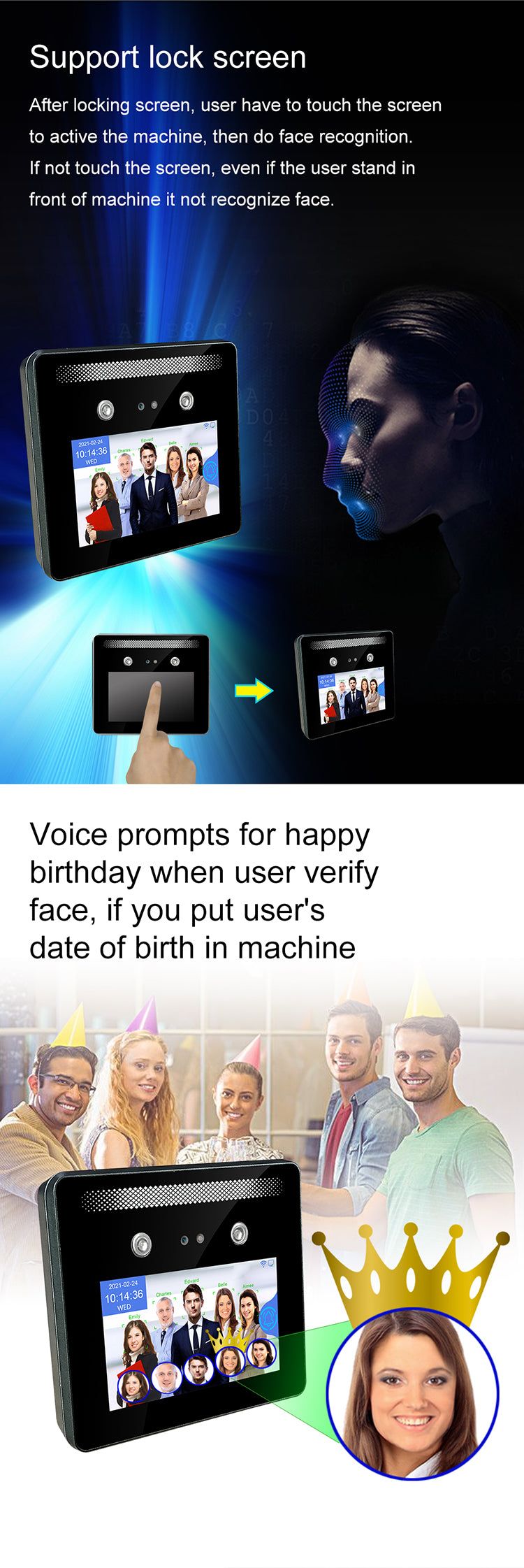
The World's First Multiple Face Detection AI Camera – Identifying Up to 5 People Simultaneously
Introducing Evolve Security Products Ltd's groundbreaking Multiple Face Detection AI Camera—the world’s first to detect up to 5 individuals at once. This cutting-edge technology brings a new level of efficiency and security to access control systems, allowing for quick, touchless identification in high-traffic environments. With advanced facial recognition, your security measures are faster, smarter, and more reliable than ever.
Types of Face Recognition Access Control Systems
Face recognition access control systems use advanced facial biometrics to identify and authenticate individuals, allowing or restricting access based on stored data. Here are the key types of face recognition systems:
-
1:1 Face Verification (Authentication)
This method compares the captured face to a specific, pre-enrolled image or database entry (e.g., matching an employee’s face to their stored profile).
Use case: Ideal for environments where known individuals require access, such as employee entry systems. -
1:N Face Identification (Recognition)
The system scans the face and matches it against a large database of images to find a match.
Use case: Perfect for scenarios where users are not pre-registered but still require access, such as in public transport or retail settings. -
Face Detection Only
This system detects the presence of a human face without verifying or identifying the individual.
Use case: Used as an initial layer in multi-factor access systems, or to trigger additional authentication steps. -
Liveness Detection
Ensures the captured face is from a live person and not a photo or video by using techniques like blinking or facial movement detection.
Use case: Typically layered with other face recognition methods to prevent spoofing and enhance security. -
Thermal & Depth Mapping Face Recognition
Combines facial recognition with thermal or depth mapping technologies to verify the 3D structure of a face, making it highly resistant to spoofing.
Use case: Commonly used in high-security environments to protect against fake 2D images. -
Emotion-Based Recognition
Analyzes facial expressions or emotions in addition to identity verification.
Use case: Though less common, it can be applied in retail or customer service environments to assess user engagement and interaction, or to monitor access control environments for stress indicators. -
Cloud-Based Face Recognition Access Control
Face data is stored securely in the cloud, enabling centralized management and cross-location access control.
Use case: Perfect for large enterprises or smart city applications that require remote monitoring and management. -
Offline Face Recognition Systems
Operates entirely offline with all data stored locally on the device, ensuring security without relying on internet connectivity.
Use case: Ideal for high-security areas or places where network connectivity is unreliable or unwanted for security reasons. -
Hybrid Access Control Systems
Combines face recognition with other biometric methods like fingerprints or iris scanning for an additional layer of security.
Use case: Best suited for environments requiring multi-layered security, such as research labs, government buildings, or banks.
Evolve Security Products Ltd – Pioneering Advanced Face Recognition Systems
At Evolve Security Products Ltd, we are at the forefront of developing market-leading face recognition systems and applications for clients worldwide. While security remains our primary focus, we are also witnessing a rise in the use of facial recognition technology for personal use, convenience, and productivity enhancement across various sectors.
For more information and to explore our full range of advanced access control solutions, visit us at:
www.facial-recognition.co.uk
www.evolvesp.net/access-control
#EvolveSecurity #FaceRecognition #AccessControl #AI #BiometricSecurity #LivenessDetection #SmartSecurity #Innovation